Eps 767: Virtualization
— The too lazy to register an account podcast
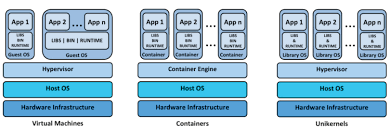
Hypervisors have traditionally been split into two classes: type one, or "bare metal" hypervisors that run guest virtual machines directly on a system's hardware, essentially behaving as an operating system.
KVM, short for kernel-based virtual machine, is a part of the Linux kernel that can run virtual machines directly, although you can still use a system running KVM virtual machines as a normal computer itself.
A virtual machine is the emulated equivalent of a computer system that runs on top of another system.
Host

Ruby Ferguson
Podcast Content
The entire stack of snapshots is virtually a single coherent disk in that sense, creating snapshots works similarly to the incremental backup technique.Nature of a nested guest virtual machine does not need not be homogeneous with its host virtual machine for example, application virtualization can be deployed within a virtual machine created by using hardware virtualization.One form of desktop virtualization, virtual desktop infrastructure VDI, can be thought of as a more advanced form of hardware virtualization.A simple VMbased architecture enables multiple users and clients. This allows you create one or two separate VMs on each side without having to rely entirely upon other vM machines.b See also
A virtual computer system is known as a "virtual machine" VM a tightly isolated software container with an operating system and application inside.Server virtualization enables multiple operating systems to run on a single physical server as highly efficient virtual machines.By completely reproducing a physical network, network virtualization allows applications to run on a virtual network as if they were running on a physical network but with greater operational benefits and all the hardware independencies of virtualization.When you use Virtual Machines for your projects or services it will be easier than ever that those who want access can easily connect them through their own devices.The following table shows how each VM's operation compares against other parts in order
Virtualization has grown into many areas including virtual desktops, virtual storage, virtual memory and more.Voil a single real megabyte of core memory on an IBM 36067, for example, could support the full 24bit address space 16 MB enabled in the machine's architecture and, properly implemented, each virtual machine could have its own full complement of virtual memory.After virtual machines and virtual memory, and the availability of these capabilities in lowcost microprocessors and PCs, the next advance was the virtualization of the desktop and the availability of applications, both singleuser and collaborative.For instance VMWare Mobile is using this technology to create new features that enable us users with high performance workloads. It also allows you access our current product development software at scale as well. The future will be defined by data protection technologies such Asynchronous File System Security Technology which allow multithreaded operations within multiple computers without any additional restrictions or limitations.1
Companies and data centers that virtualize will improve their reputation while also enhancing the quality of their relationship with customers and the planet.Virtualizing hardware and software means that a company does not need to depend on a vendor for these physical resources.In a virtual environment, users lose control of what they can do because there are several links that must collaborate to perform the same task.On top Virtualization is critical in ensuring customer support. If you have problems or other issues your product could be impacted by this process please contact Customer Support at 180074300 1 746 077 e3 U, we would like all companies involvedit's important if an issue arises from such things as computer equipment failure without incident.